Password reset flows need to be reliable. Once a user clicks Forgot password, it should only take a few moments until they get the information they need to continue logging in to your product.
If this process breaks and the email never shows up, the user has to try again, gets frustrated, and may have to file a support ticket, or worse, leave altogether.
That’s why ensuring this simple flow works reliably needs to be a top priority. There are many reasons a password reset email may not be delivered properly, but luckily it’s almost always the result of concrete, diagnosable problems in your sending pipeline.
This guide breaks down the seven most common reasons password reset emails fail to reach the inbox, and how to diagnose and fix each one. Before we look at each reason individually, it’s helpful to review the basics of how emails are routed and delivered.
Understanding the email delivery pipeline
A password reset email goes through many steps before it reaches a user. The entire chain has to work perfectly:
- Your application triggers the event. A backend call fires an SMTP/API request to your ESP.
- Your Email Service Provider (ESP) processes and sends the email. ESP queues, formats, applies routing rules, and pushes it out.
- The recipient’s mail server evaluates it. SPF, DKIM, and DMARC checks fire. The receiving ISP decides if you’re legitimate.
- Spam filters scan content and reputation. Anything suspicious increases filtering or rejection.
After all that, the message will either land in your recipient’s inbox, spam, quarantine, or may never arrive at all.
It’s important to remember that “sent” does not mean “delivered.” While your ESP may show a successful “sent” status, that only means the message left the ESP’s system. It does not guarantee its arrival in your recipient’s inbox.
The majority of failures occur after your ESP hands off the message, meaning you can’t rely on that status as proof of delivery. Understanding these failure points will help you diagnose and solve deliverability issues with missing password reset emails.
The top 7 reasons your password reset emails aren’t arriving
Missing or misconfigured authentication (SPF, DKIM, DMARC)
The problem
Your domain’s SPF, DKIM, or DMARC records are missing or incorrect. These are the mechanisms ISPs use to verify that you’re a legitimate sender. If any of these fail, your message goes straight to spam or gets rejected.
Why it matters
Most popular email clients, including Gmail, Outlook, Yahoo, and iCloud, now enforce authentication as a prerequisite for inbox placement. Missing or misconfigured records are among the leading causes of dropped transactional emails.
How to diagnose
Start by verifying whether mailbox providers actually trust your domain. You can validate this with real tests and concrete signals.
- Run your domain through MXToolbox SPF/DKIM/DMARC check.
- You can also inspect your current SPF record by running
dig TXT yourdomain.comin your terminal. - Send a test email to mail-tester.com.
- Look for
SPF fail,DKIM fail, orDMARC failin your ESP logs.
The fix
After confirming the problem, explicitly repair each layer of your authentication stack so ISPs can reliably validate your messages:
- Add SPF including your ESP:
v=spf1 include:sendgrid.net ~all. - Add DKIM keys provided by your ESP.
- Implement a DMARC policy:
v=DMARC1;p=none;rua=[mailto:[email protected]](mailto:[email protected]). - Then move to
p=quarantineorp=rejectonce stable.
Once SPF, DKIM, and DMARC are all passing consistently, you remove one of the biggest structural reasons password reset emails never make it to the inbox.
Poor domain reputation
The problem
Your domain reputation determines whether an ISP trusts you and therefore is a critical factor for email deliverability. It can be damaged by any one of the following reasons:
- High bounce rates.
- Spam complaints.
- Sending to purchased lists.
- Being listed on DNS-based blacklists.
Why it matters
Even a single spike in spam complaints can tank your deliverability. Gmail’s thresholds are unforgiving—anything above 0.3% complaint rate is considered high risk.
How to diagnose
Start by validating whether mailbox providers still trust your domain:
- Review Google Postmaster Tools reputation report.
- Run an MXToolbox blacklist check.
- Inspect complaint rates in your ESP (target: <0.1%).
The fix
Once you confirm a reputation problem, address it systematically. Restoring domain trust requires removing sources of abuse and follow best practices:
- If blacklisted, identify the root cause and request removal.
- Always remove hard bounces immediately.
- Implement a suppression list to avoid re-sending to complainers.
- Never send emails to purchased or scraped lists.
- Use dedicated subdomains for transactional email (
auth.yourdomain.com). This isolates failures and protects your primary domain’s reputation.
Unfortunately, reputation recovery can be slow. Try to follow best practices from the start to prevent damage upfront.
Using “no-reply” sender addresses
The problem
Sending from [email protected] signals low legitimacy. Spammers use no-reply addresses because they don’t want responses, and ISPs know this.
Why it matters
These addresses increase spam filtering probability, and they limit users’ ability to reply when something is broken, resulting in more spam reports.
How to fix
Make sure you’re not sending emails from a noreply@ email address. Instead, use monitored inboxes, such as hello@ or security@.
Your email content triggers spam filters
The problem
Even if your email authentication is set up perfectly, sometimes the content of the email itself can trigger spam filters.
Common spam triggers include:
- Too many links.
- URL shorteners.
- ALL CAPS subject lines.
- Promotional wording in a transactional message.
- Image-heavy layouts.
- Missing plain-text version.
- Link tracking redirecting through suspicious domains.
Why it matters
Password reset emails contain links by necessity, but poor formatting or unnecessary elements can increase the likelihood of them being marked as spam.
How to diagnose
There are a few ways to test whether your email content is triggering filters:
- Send your email through SpamAssassin.
- Review spam-folder placements for major ISPs.
- Check link rewriting configuration in your ESP.
The fix
For transactional emails, try to always simplify the message and remove non-essential elements:
- Make sure you’re including only a single link.
- Keep text minimal for functionality over aesthetic.
- Use your own domain for reset links.
- Include a plain-text version.
- Avoid promo language entirely.
- Keep email size <102KB.
You'll also want to be careful how you phrase your subject lines.
Instead of:
URGENT: Reset Your Password NOW!!!
Use:
Reset your password
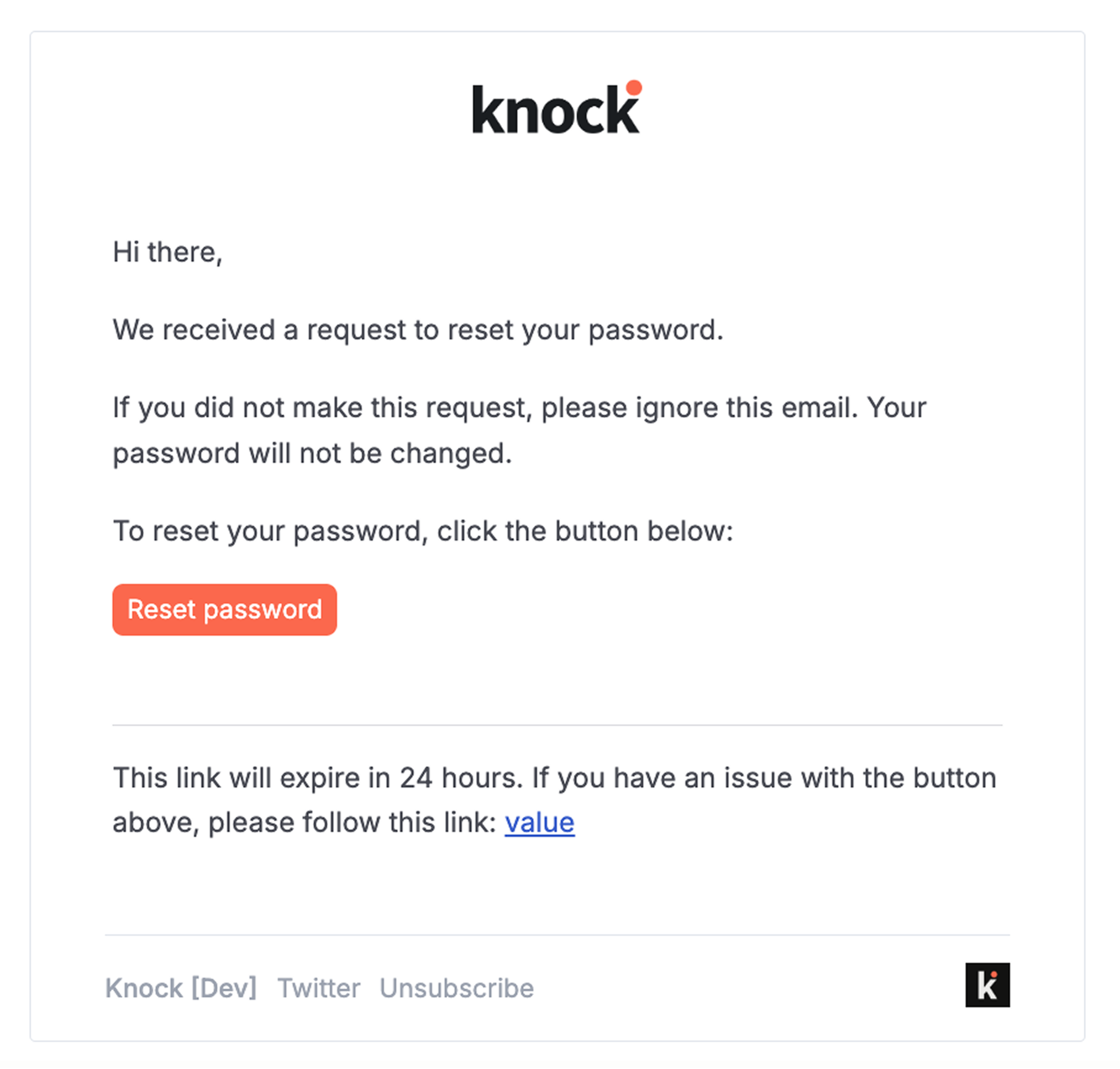
Here's a good example of a standard password reset email you can copy:
High bounce rates from bad email data
The problem
High bounce rates degrade your entire domain’s deliverability. To prevent bounces, ensure your user database doesn’t contain any of the following:
- Email addresses with typos.
- Deactivated email accounts.
- Dead domains.
- Role-based addresses (
info@,admin@).
Why it matters
ISPs treat high bounce rates as proof you’re not maintaining data hygiene. Once flagged, your deliverability can take a hit.
How to diagnose
Start by determining whether bad email data is undermining your deliverability:
- Review bounce breakdowns in your ESP.
- Check patterns (misspellings, outdated providers).
- Identify repeated soft bounces from the same recipients.
The fix
Once you confirm that bad data is the source of bounces, strengthen your acquisition and suppression systems so invalid addresses never reach your sending pipeline:
- Implement real-time email validation at signup.
- Auto-suppress hard bounces.
- Use double opt-in where applicable.
- Monitor soft bounce trends weekly.
Bad data doesn’t correct itself—your system has to enforce strict hygiene or your deliverability will collapse over time.
Rate limiting and throttling issues
The problem
Your ESP or the recipient ISP may throttle your messages due to volume spikes or rate limits, meaning your message doesn't make it to your recipient’s inbox.
Why it matters
Password reset emails are time-sensitive, so even a small delay can lock a user out of their account.
How to diagnose
Start by confirming whether your messages are getting slowed down or rejected due to volume spikes or ISP throttling. Rate limiting issues often appear as delays rather than outright failures, so you need to inspect the signals carefully:
- Look for 421/451 SMTP responses.
- Check ESP logs for rate limit events.
- Measure time-to-inbox (target: <10 seconds).
The fix
Once you confirm rate limiting is in play, you’ll need to increase your system’s capacity and add resilience around delivery failures:
- Upgrade your ESP’s rate limit tier.
- Add retry logic with exponential backoff.
- Distribute traffic across multiple IPs for scale.
- Warm up new domains and IPs gradually.
ISP-specific filtering rules
The problem
Deliverability isn’t uniform, it’s ISP-specific. Your email might pass Gmail but fail Outlook or Yahoo because each ISP uses different filtering models.
Why it matters
A single-ISP blind spot creates inconsistent user experiences and unpredictable support load.
How to diagnose
Isolating which ISPs have delivery failures will take some manual testing:
- Segment email performance by domain.
- Test across Gmail, Outlook, Yahoo, iCloud.
- Review Google Postmaster Tools + Microsoft SNDS.
The fix
If you can pinpoint an ISP, adapt your sending patterns and content so that provider stops flagging your messages:
- Customize content or formatting for problematic ISPs.
- Adjust sending patterns if one ISP throttles unexpectedly.
- Use seed lists for ongoing monitoring and test frequently.
How to monitor and maintain email deliverability
Deliverability doesn’t stay stable on its own. It drifts, degrades, and breaks unless you track it with the same discipline you apply to uptime or API error rates. Treat this as part of your core reliability surface area, not a “marketing metric.”
Track the metrics that signal early failures
Start by measuring the indicators that expose friction before users notice it. These numbers give you the first warning that something in your sending pipeline is slipping:
- Delivery rate. Aim for 98%+ to confirm messages are consistently accepted.
- Bounce rate. Keep it under 2% to avoid reputation damage.
- Spam complaint rate. Maintain <0.1% to stay within ISP tolerances.
- Time-to-inbox. Target <30 seconds for authentication emails.
- Authentication pass rate. Anything less than 100% signals DNS or key issues.
Use these metrics as your ongoing health baseline. Any movement outside these ranges warrants immediate investigation.
Use tools that expose ISP-level problems
Your ESP won’t show you all of the details that matter for deliverability. Use tools that surface reputation, rate-limiting, and filtering behavior across ISPs.
- Google Postmaster Tools. Track Gmail reputation, spam rate, and authentication health.
- Microsoft SNDS. Monitor Outlook-specific filtering and IP reputation.
- ESP analytics dashboards. Review bounce codes, spam complaints, and inbox placement.
- Validity / 250ok. Add deeper insight into seed tests, ISP filtering, and domain reputation.
These tools give you visibility into issues you won’t find by looking at aggregate ESP stats alone.
Configure alerts that catch issues before users do
Don’t wait for support tickets to know you have a problem. Setting automated alerts that fire the moment deliverability weakens will help you fix issues quickly.
- Delivery rate drops below 95%.
- Bounce rate spikes unexpectedly.
- Spam complaints climb above normal thresholds.
- Any SPF, DKIM, or DMARC failures appear.
Review performance before problems compound
A quick weekly review, even 10 minutes of data inspection, can prevent long-tail failures. You’ll catch issues early, protect your domain reputation, and avoid the cascading impact of slow or missing authentication emails.
Checklist: Preventing email delivery failures
It’s easy to get into the habit of only addressing deliverability after something breaks. This checklist forces you to address the structural issues before they turn into user lockouts, support tickets, or long-term reputation damage.
Set up authentication
- Ensure SPF, DKIM, and DMARC are fully configured and validated.
- Monitor authentication pass rates daily and resolve failures immediately.
Use a dedicated subdomain
- Route all authentication emails through a dedicated domain (e.g.,
auth.yourdomain.com). - Isolate transactional traffic to protect your primary domain’s reputation.
Choose ESPs built for deliverability
- Select providers optimized for transactional performance (Postmark, Mailgun, Resend).
- Prioritize routing speed, uptime guarantees, and time-to-inbox.
Follow content best practices
- Keep designs minimal and remove non-essential formatting.
- Use a single, unambiguous CTA in both HTML and plain-text versions.
- Write a neutral, predictable subject line (“Reset your password”).
- Avoid promotional language, unnecessary links, or tracking that triggers filters.
Monitor actively
- Set alerts for delivery dips, bounce spikes, and authentication failures.
- Track time-to-inbox for major ISPs and investigate delays.
- Review bounce and complaint rates every week and suppress bad addresses.
Implement fallback options
- Enable SMS or push as backup channels when email delivery fails.
- Offer authenticator app codes to bypass email entirely.
- Expose a clear support workflow from the reset page for users who can’t receive email.
Send reliable transactional emails with Knock
Authentication emails are high-stakes. Every failure erodes trust and blocks access. Using an unreliable email delivery pipeline to power one of the most sensitive user flows in your product is a structural liability, not a cost-saving measure.
A dedicated notification platform addresses the structural shortcomings that DIY systems inevitably develop. Instead of chasing individual failures, you shift to a system built to prevent them:
- Deliverability monitoring baked in.
- Auditable logs across all channels.
- Template versioning.
- User preferences.
- Unified analytics.
If you’re hitting structural limits with your current setup, consider offloading the complexity altogether. Knock handles the entire notification pipeline, including transactional email deliverability, so teams can stop debugging SMTP and get back to focusing on building a great product.
Whether you’re sending password reset emails or other transactional messaging, Knock can help. If you'd like to try it out, you can sign up for a free account or chat with our team. 👋